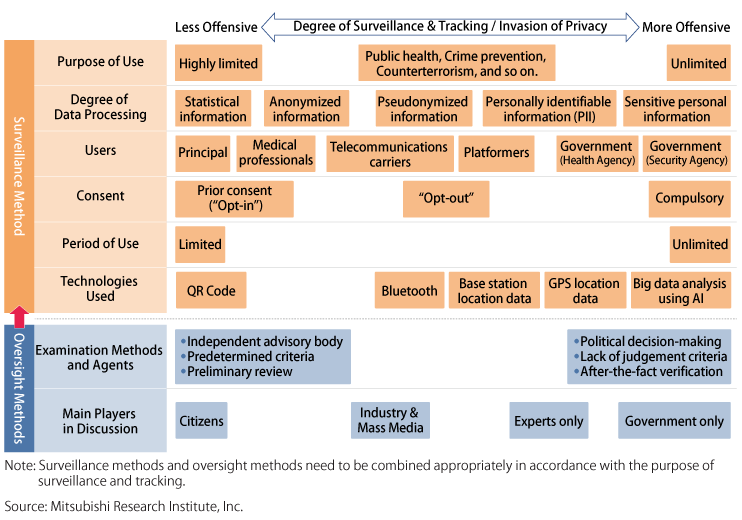
Against this threat, it is important to clarify beforehand the criteria for using personal information in the case of emergencies. Each successive crisis brings the risk of personal information being gradually compromised under the exigencies of political decision-making. It also becomes necessary to halt the continuation of government surveillance introduced as emergency measures.*2 We must determine how to check the power of surveillance methods employed in “emergency situations” (Figure). Specifically, by clarifying the purposes for which surveillance will be used and selecting the corresponding appropriate technology, we can design a framework for the surveillance method that specifies details such as the usage period, degree of data processing, and users. Moreover, it is also necessary to establish appropriate audit methods in accordance with these surveillance technologies’ intrusion on privacy.
It should be noted that consent from the individual is not always needed when securing a swift and effective response to crisis. Japan’s Act on the Protection of Personal Information does not require a person’s consent in cases in which the provision of personal data is based on laws and regulations; when there is a need to protect the life, body or property of an individual; or cases in which there is a special need to promote public health.*3 However, the government is expected to inform the public of this fact in advance.
With the introduction of surveillance technologies that deploy AI, threats to personal information will increase even more. In order to realize a “Safe Information Society”, systems must be designed in accordance with advances in information technologies and must also enhance due process and promote citizens’ independent and proactive review. Having experienced major changes prompted by COVID-19, it is essential that government, industry, and private individuals debate these issues while an independent advisory body made up of experts in information technology and personal information protection takes part in the decision-making process.
*1:For example, China and South Korea use GPS location data, and Israel uses location data from mobile phones which has been used in counterterrorism operations by its security agency. Surveillance efforts in Hong Kong and Taiwan make use of location data from digital signals emitted by mobile phones that use a virtual fence mechanism surrounding quarantined areas. South Korea and Hong Kong also use electronic wristbands linked with the technologies mentioned above. In Singapore, authorities use a Bluetooth-enabled app developed by the government, and European countries have also begun developing their own Bluetooth-enabled apps. Google and Apple are jointly developing a contact tracing app and several countries, including the UK and Germany, have shown an interest in implementing this tool.
*2:The European Commission issued a “Recommendation” to EU member states indicating that the use of contact tracing apps should not be made mandatory and that limited periods of use should be set. Discussions are also taking place at the European Parliament concerning the limited use of anonymous data and prohibitions against its storage in a centralized database.
*3:Act on the Protection of Personal Information (Personal Information Protection Law) Article 16, paragraph (3), items (i) to (iv) and Article 23, paragraph (1), items (i) to (iv).